The SUI ecosystem DEX #Cetus has been attacked. Is code security auditing really enough?
The reasons and impacts of the attack on Cetus are still unclear, but we can first look at the code security audit situation of Cetus.
As outsiders, we may not understand the specific technology, but we can comprehend this audit summary.
➤ Certik's Audit
Looking at it, Certik's code security audit of Cetus found only 2 minor risks, which have been resolved. There are also 9 informational risks, 6 of which have been resolved.
Certik gave an overall score of 83.06, with a code audit score of 96.
➤ Other Audit Reports of Cetus (SUI Chain)
Cetus has listed a total of 5 code audit reports on its GitHub, excluding Certik's audit. It seems the project team knows that Certik's audit is merely formal, so they did not include this report.
Cetus supports both Aptos and SUI chains, and these 5 audit reports come from MoveBit, OtterSec, and Zellic. MoveBit and OtterSec audited Cetus's code on the Aptos and SUI chains, respectively, while Zellic also audited the code on the SUI chain.
Since the attack occurred on Cetus on the SUI chain, we will only look at the audit reports for Cetus on the SUI chain.
❚ Audit Report from MoveBit
Report uploaded to GitHub on: 2023-04-28
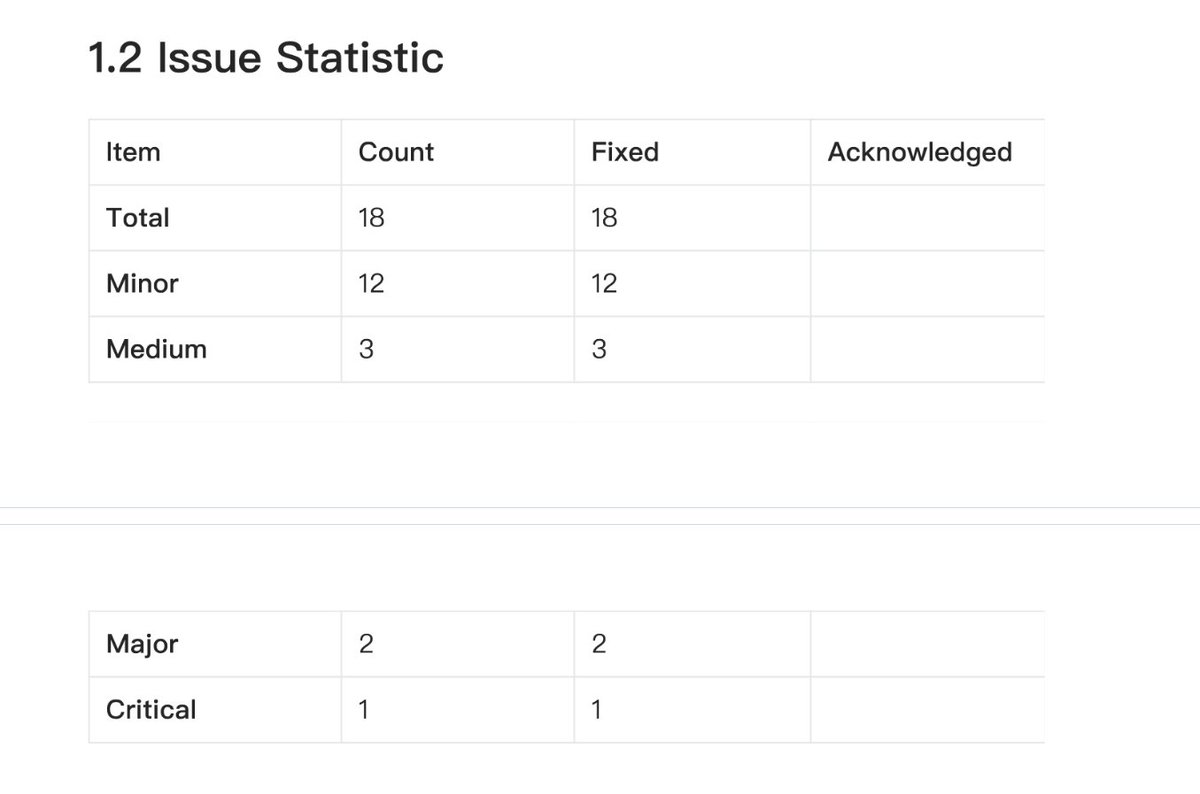
If we cannot understand the specific audit content, we can find a table like this to see the number of risk issues listed in the report at various levels and their resolution status.
MoveBit's audit report for Cetus found a total of 18 risk issues, including 1 critical risk issue, 2 major risk issues, 3 moderate risk issues, and 12 minor risk issues, all of which have been resolved.
This is more than the issues found by Certik, and Cetus has resolved all these issues.
❚ Audit Report from OtterSec
Report uploaded to GitHub on: 2023-05-12
OtterSec's audit report for Cetus found 1 high-risk issue, 1 moderate risk issue, and 7 informational risks. Since the report's table does not directly show the resolution status of the risk issues, I won't include a screenshot.
Among them, the high-risk and moderate-risk issues have been resolved. For the informational risk issues, 2 have been resolved, 2 have submitted patches, and there are 3 remaining. After some research, these 3 are:
• The inconsistency between Sui and Aptos version codes, which may affect the accuracy of liquidity pool price calculations.
• Lack of pause state verification, meaning that during a swap, there is no verification of whether the liquidity pool is in a paused state. If the pool is paused, trading may still be possible.
• Converting u256 type to u64 type, which can cause overflow if the value exceeds MAX_U64, potentially leading to calculation errors during large transactions.
It is currently uncertain whether the attack is related to these issues.
❚ Audit Report from Zellic
Report uploaded to GitHub on: April 2025
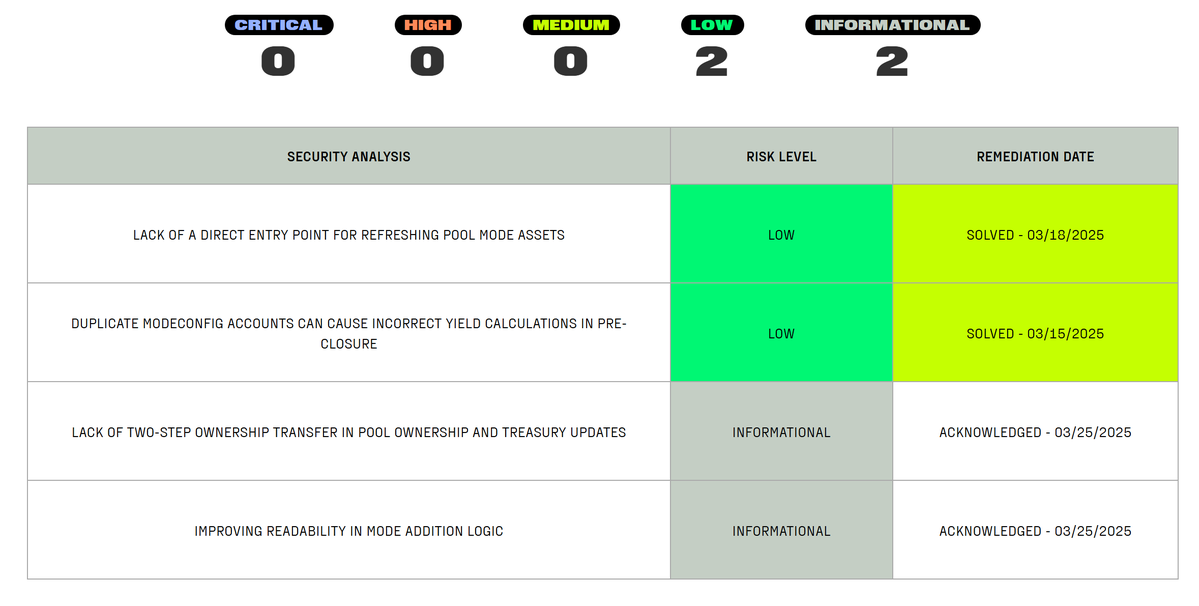
Zellic's audit report for Cetus found 3 informational risks, none of which have been fixed:
• A function authorization issue that allows anyone to call and deposit fees into any partner account. This seems to pose no risk, as it is depositing money, not withdrawing it. Therefore, Cetus has not fixed this for now.
• There is a function that has been deprecated but is still referenced, which is code redundancy. It seems to pose no risk, but the code is not very standardized.
• A UI presentation issue in NFT display data, which could have used a character type but Cetus used a more complex TypeName data type in the Move language. This is not a significant issue and may lead to future NFT functionalities.
Overall, Zellic found 3 ozone layer sub-issues, which are basically low-risk and pertain to code standardization.
We should remember these three auditing firms: MoveBit, OtterSec, and Zellic. Most auditing firms in the market are skilled in EVM audits, while these three specialize in Move language code audits.
➤ Audit and Security Levels (Using New DEX as an Example)
First, projects that have not undergone code audits carry a certain Rug risk. After all, if they are unwilling to spend money on audits, it is hard to believe they have long-term operational intentions.
Second, Certik audits are essentially a form of "favor-based auditing." Why do I say it is "favor-based auditing"? Certik has a very close partnership with CoinMarketCap. On the project page of CoinMarketCap, there is an audit icon that leads to Certik's navigation platform, Skynet.
As CoinMarketCap is a platform under Binance, it indirectly establishes a partnership between Certik and Binance. In fact, Binance and Certik have always had a good relationship, so most projects wanting to list on Binance will seek Certik's audit.
Thus, if a project seeks Certik's audit, it is highly likely that they want to list on Binance.
However, history has shown that projects audited solely by Certik have a high probability of being attacked, such as DEXX. Some projects have even already FUGed, like ZKasino.
Of course, Certik also provides other security assistance; not only do they conduct code audits, but they also scan websites, DNS, etc., providing some security information beyond code audits.
Third, many projects will seek one or more other quality auditing entities for code security audits.
Fourth, in addition to professional code audits, some projects will also conduct bug bounty programs and audit competitions to gather ideas and eliminate vulnerabilities.
Since the attacked product is a DEX, let's take some newer DEXs as examples:
---------------------------
✦✦✦ GMX V2, audited by 5 companies including abdk, certora, dedaub, guardian, and sherlock, and launched a single maximum bug bounty program of $5 million.
✦✦✦ DeGate, audited by 35 companies including Secbit, Least Authority, and Trail of Bits, and launched a single maximum bug bounty program of $1.11 million.
✦✦✦ DYDX V4, audited for code security by Informal Systems, and launched a single maximum bug bounty program of $5 million.
✦✦✦ hyperliquid, audited for code security by hyperliquid, and launched a single maximum bug bounty program of $1 million.
✦✦ UniversalX, audited by Certik and another expert auditing agency (the official audit report has been temporarily removed).
✦ GMGN is special; no code audit report was found, only a single maximum bug bounty program of $10,000.
➤ In Conclusion
After reviewing the code security audit situations of these DEXs, we can see that even a DEX like Cetus, which has been audited by three auditing agencies, can still be attacked. Multi-entity audits, combined with bug bounty programs or audit competitions, provide relatively assured security.
However, for some new DeFi protocols, there are still unresolved issues in the code audits, which is why Brother Bee is particularly concerned about the code audit situations of new DeFi protocols.
How safe are the DeFi projects that people are crazy about getting involved in their funds?
Safety is no small matter!
Especially for DeFi/PayFi/RwaFi products, where user funds are deposited or authorized, security is always the first and most important.
Mature DeFi products such as Uniswap, GMX, and DyDx have been tested by the market (hackers) for a long time, and their security is relatively higher.
However, there is a higher level of uncertainty in new DeFi applications. That's why, new DeFi products, will have a relatively higher yield or airdrop return. Because it's a risk compensation for early participants.
Although code security audits cannot fully guarantee its security, it can relatively ensure security. In this article, we will take a look at several new DeFi/PayFi/RwaFi ...... Security management such as code audit of similar products.
➤Huma @humafinance
❚ Project Introduction
Huma is a PayFi project based on the Solana ecosystem and Stellar, which aims to reinvent payments, yields, and financing on the blockchain.
❚ Ecological scale
At present, Huma is ahead of the TGE, and there is a cap on the size of funds for ecological participation.
According to Huma's official website, the protocol currently has a total active liquidity of $104 million and a total trading volume of $4.3 billion.
❚ Code auditor: Halborn
Founded in 2019, Halborn has audited the code of many similar projects such as public chains and DeFi, such as: Thorchain, Taiko, Core Chain, Story, Plume, Solayer, Zetachain, Avalanche, Persistenct, etc.
❚ Audit report
According to the audit report, Huma identified a total of 2 low-risk issues that have been resolved. 2 informational risks are known. No moderate or upper risk was identified.
❚ Bug bounties and security contests
In July 2026, Huma launched a $50,000 bug bounty program on the cantina platform.
Cantina is a Web3 security marketplace platform founded in 2023 that offers security services such as security contests, bug bounties, security reviews, and more. Well-known projects such as Uniswap, Morpho, Pendle, PancakeSwap, and others have launched bug bounty programs or security contests on them.
➤DefiApp @defidotapp
❚ Project Introduction
DefiApp is an aggregated DeFi based on chain abstraction, including spot swap, perpetual futures, and lending applications.
❚ Ecological scale
According to DeFillama, DefiApp has a 24-hour aggregate trading volume of $137.38 million. The highest daily aggregate trading volume was $225.76 million.
❚ Code auditors
The DefiApp documentation shows that different parts are audited by different agencies:
✦ Infrastructure Section: Sela
Sela is a cloud security services organization whose partners include Microsoft, Google, AWZ, and Alibaba.
✦ Web Application Section: Halborn
✦ Smart contract part: Cantina
✦ Airdrop part: pashov
Pashov Audit Group is a blockchain security company that has audited projects such as DeFi, Gaming, and Chain Split, such as Sushi, 1inch, Aave, Ethena, Radiant, and more.
❚ Audit report
The code audit report link in the DefiApp documentation is linked to its Github, but the link cannot be opened, and no audit report can be found in its Github.
Not sure if you haven't completed your audit yet? Or has it not been submitted to Github yet? @defidotapp
On the websites of the listed auditors, only pashov's audit report on DefiApp, that is, the audit of the airdrop part, was found.
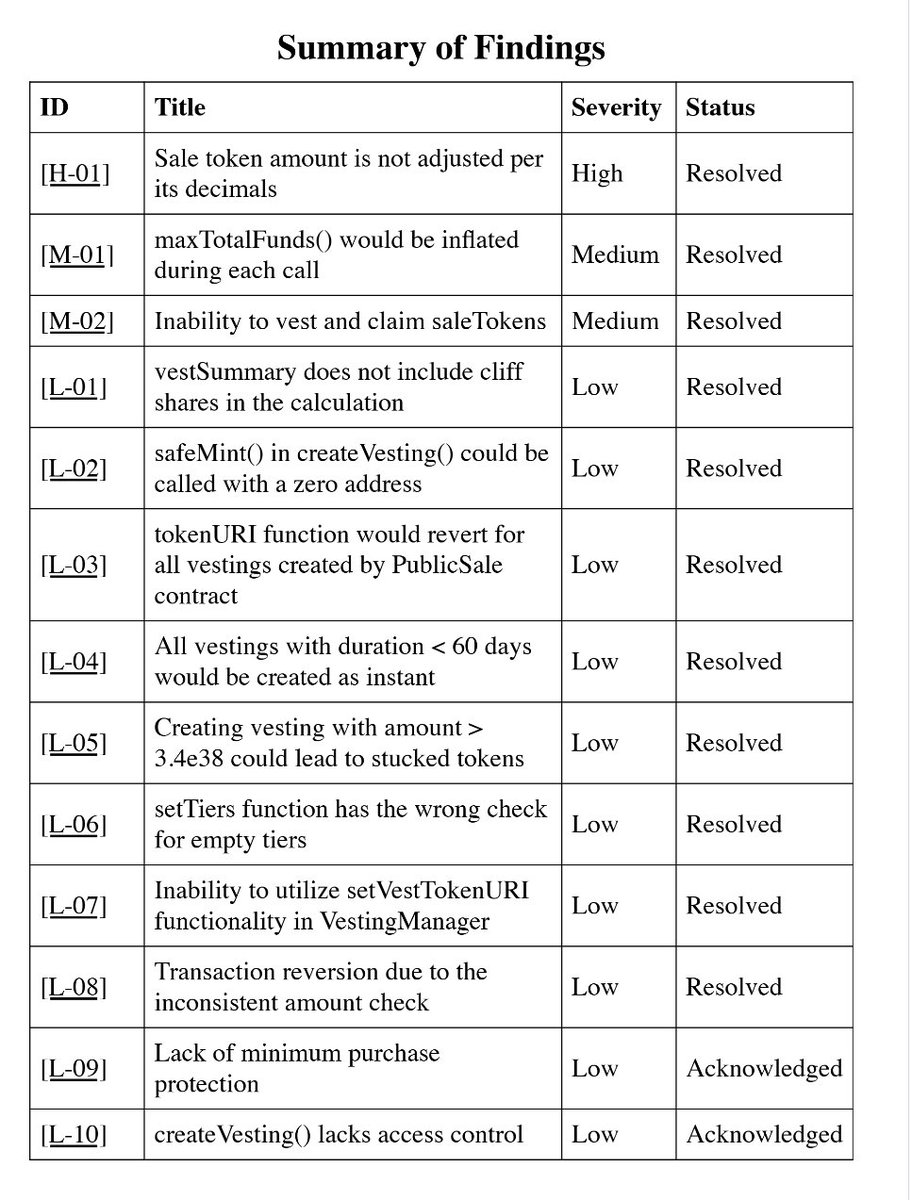
Pashov's audit report shows that DefiApp airdropped part of the code, and found a total of 1 high-risk, 2 medium-risk, and 10 low-risk. All but 2 low-risk issues were resolved.
➤StandX @StandX_Official
❚ Project Introduction
Perpetual futures DEX, currently known to support Solana and BSC chains.
❚ Ecological scale
According to StandX's official website, StandX has $TVL2297 million, a total of 30,468 transactions on the chain, and 7,798 active participants.
❚ Code auditors
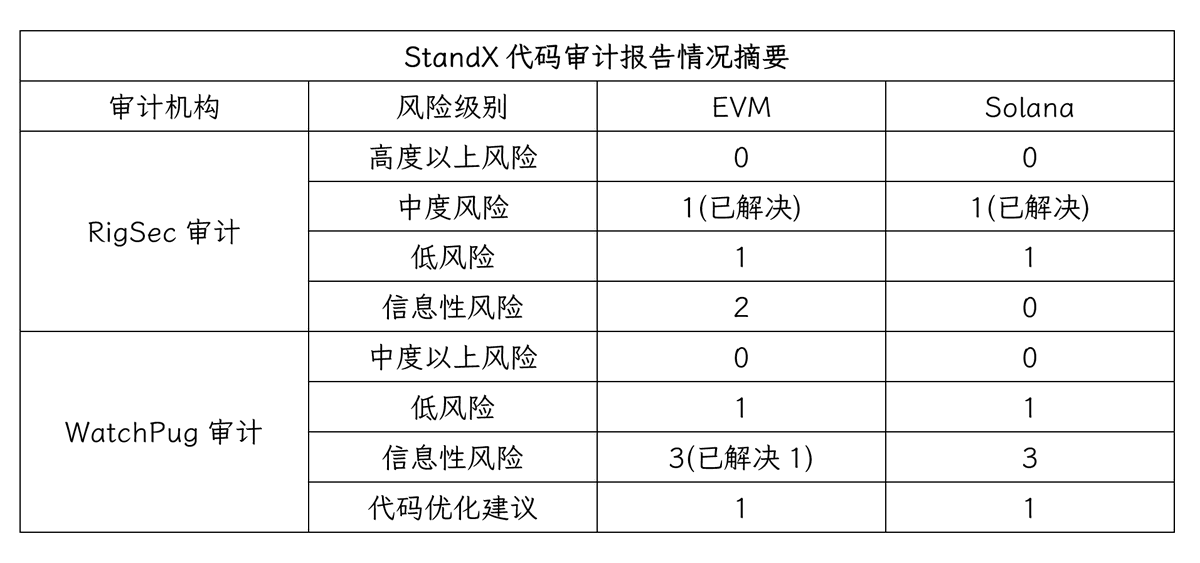
StandX's code consists of two parts, the EVM chain and the Solana edge, all of which are double-audited by RigSec and WatchPug.
RigSec is a company focused on digital asset security, and its main market is currently in Asia, and its audited projects include edgeX Exchange.
WatchPug is a blockchain security audit company focused on code auditing of DeFi protocols, NFT projects, and Web3 applications. Audited projects include Equilibria Finance, Penpie, and others.
❚ Audit report
StandX's solana and EVM chaincode were audited by 2 auditors, and the report showed that all moderate or higher risks were addressed. There are several low-risk, informational risks, and code optimization recommendations.
➤ Write at the end
Overall, Huma is a bit more secure. Not only is the risk level found in the code audit report lower, but the bug bounty program has been running for nearly one year. This may explain why Huma fills up in less than 1 hour every time Huma develops a deposit. The security awareness of large funds is still relatively high.
StandX's 4 audit reports show that the risk level is relatively low and above moderate is resolved. However, the two code audit companies that conducted the audit are relatively well-known, and there is a certain uncertainty about the security of StandX.
As for DefiApp, it is possible that the audit speculation of other parts except for the airdrop contract may not be completed yet. Or maybe the audit has been completed and the team is working on a fix for the issue.
Finally, for a new DeFi product, even if it passes a code security audit, it still can't be sure that it is fully secure.
Remind everyone to be cautious when participating in early Defi projects, and be even more cautious in operation!
39
32.68K
The content on this page is provided by third parties. Unless otherwise stated, OKX is not the author of the cited article(s) and does not claim any copyright in the materials. The content is provided for informational purposes only and does not represent the views of OKX. It is not intended to be an endorsement of any kind and should not be considered investment advice or a solicitation to buy or sell digital assets. To the extent generative AI is utilized to provide summaries or other information, such AI generated content may be inaccurate or inconsistent. Please read the linked article for more details and information. OKX is not responsible for content hosted on third party sites. Digital asset holdings, including stablecoins and NFTs, involve a high degree of risk and can fluctuate greatly. You should carefully consider whether trading or holding digital assets is suitable for you in light of your financial condition.

